Data Reporting
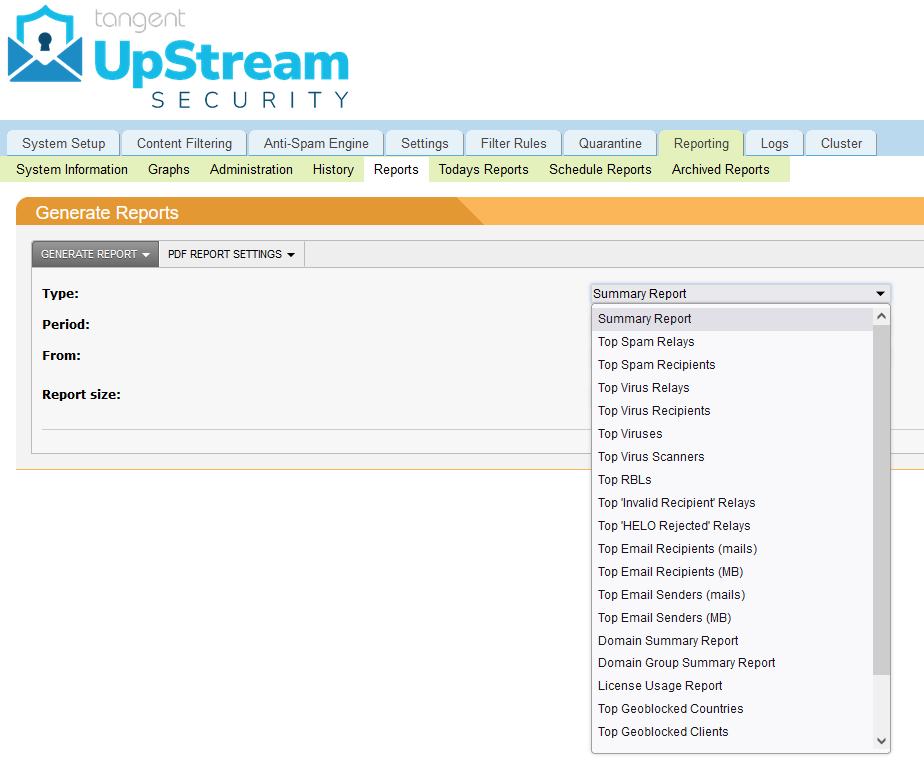
UpStream provides a series of different reports for domain administrators to get an idea of what kinds of threats are being sent towards their organization, which users are being most heavily targeted and even the origins of these attacks, broken out by country, server and even individual senders.
Armed with this threat intelligence, curated decisions can be made on fine tuning features like Geoblocking, IP range blockades and additional training and advisory for targeted users to best avoid the latest phishing and scam attempts they may be subject to.
These reports can be scheduled to automatically be created for a selected time interval and sent to the administrator for review without them ever having to log into the system.
A handful of examples are available below, along with a partial listing of different options.
Commonly used reports include:
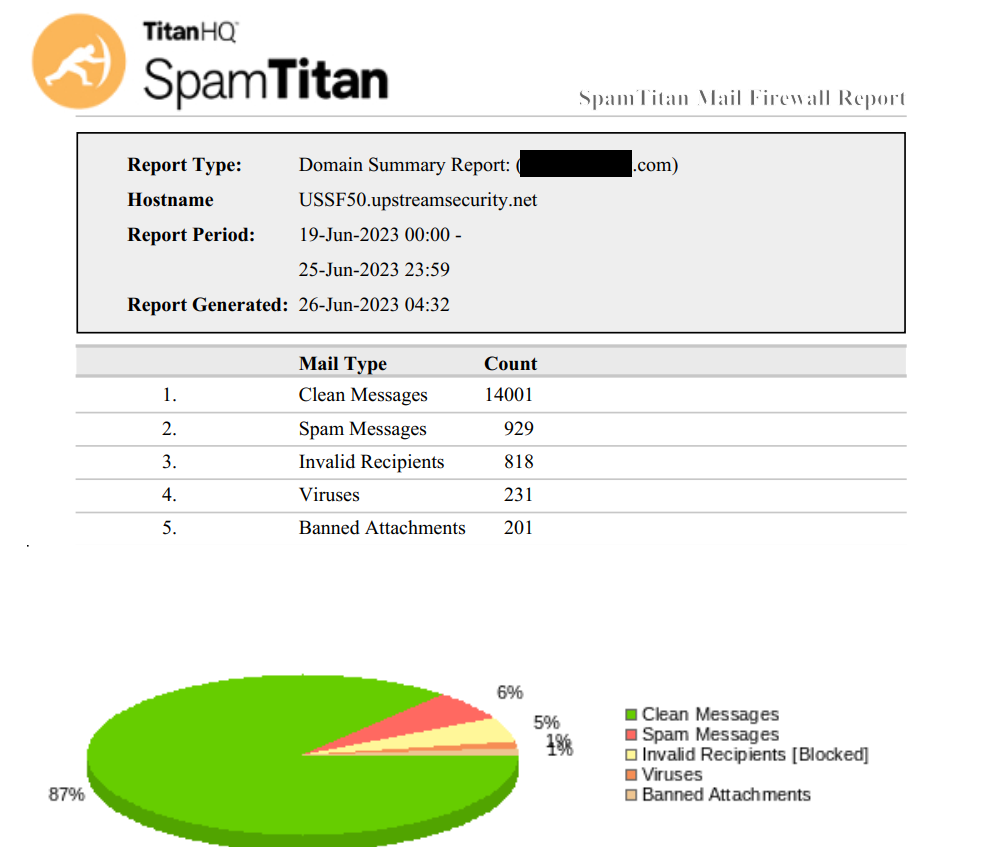
Executive summaries, like the Domain Summary Report, which breaks out how many clean messages were delivered versus virus laden, spam or policy-blocked messages that were dropped by UpStream. In the never ending battle for IT Budgets, being able to see where exactly how your systems are performing is critical.
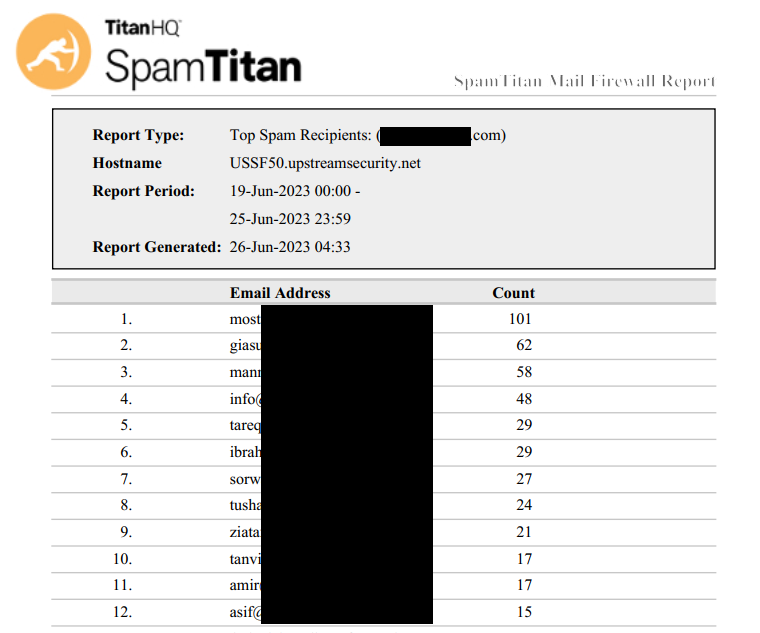
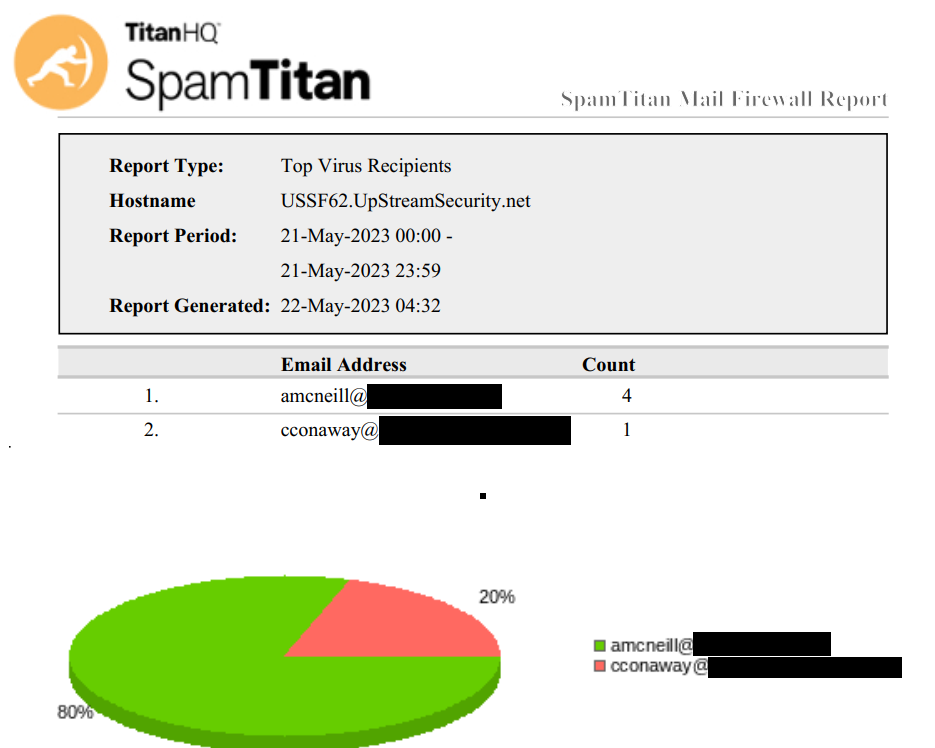
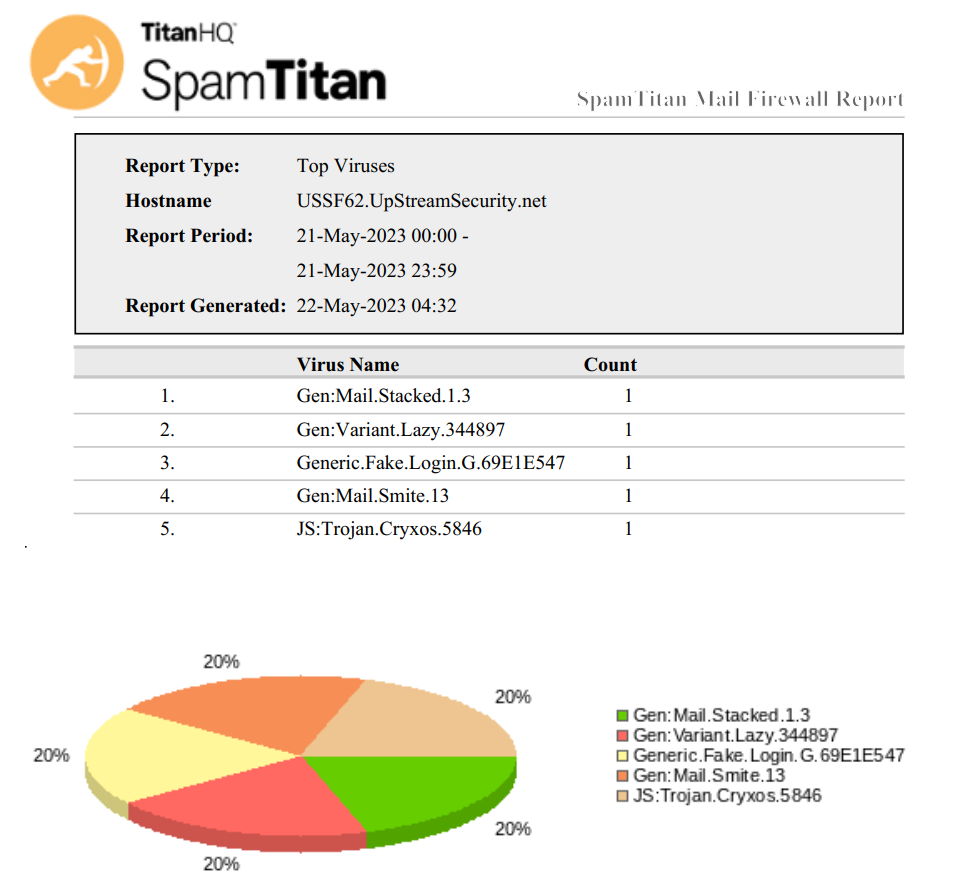
Top Virus Recipients, showing which users are being targeted by viruses, malware and worms more often than others. Such users may be the public faces of the organization or have simply had their contact information leaked or scraped previously, but the more people know about them, the more often they’ll be attacked and often with more advanced spearphishing attacks. These users should be given extra attention in terms of security training on how to spot phishes and scams.
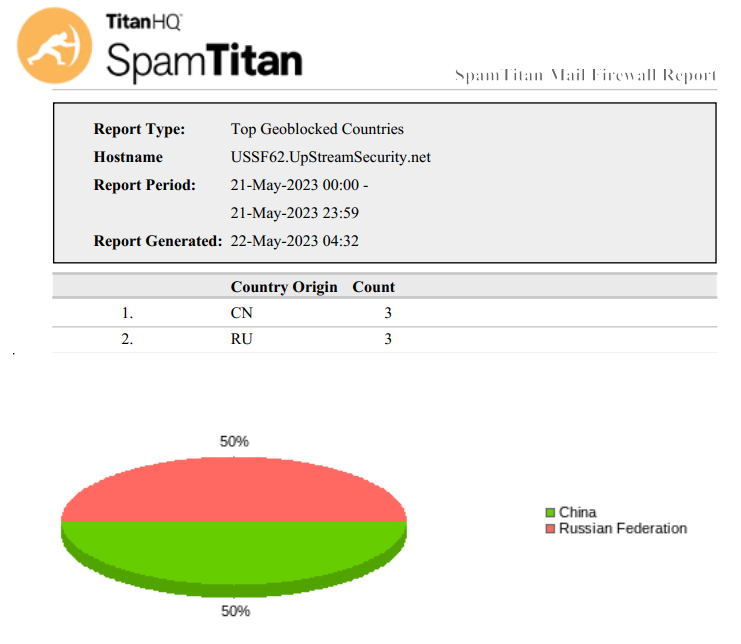
Top Geoblocked Countries, another executive report, show which countries host the majority of attackers and spammers that have been targeting your organization and can be used to show threat growth over time. For organizations that are potential supply chain attack targets or hold intellectual property that may be of interest to others, this can be used as a helpful justification for further security software enhancements internally.